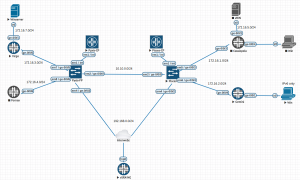
Yesterday, as part of my JNCIE-SEC Training, I reviewed NAT64 with the following Topology:
I pinged from Win to Winserver with Traffic going over Gemini(vSRX 15.1X49-D120), Pisces (vMX 17.3R1-S1.6), Pyxis (vMX 17.3R1-S1.6) and Virgo (vSRX 15.1X49-D120).
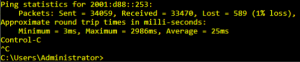
So far everything seems to run fine – sometimes a single ping gets dropped but with 1% loss this is okay for me:
For me the D120 runs stable and so far I did not experience any problems.
Below I pasted the configs in case anyone wants to recreate this Lab:
Gemini:
set version 17.3R1-S1.6 set system host-name Gemini set system root-authentication encrypted-password "$6$JlBYr7De$HiDZ2uPKQrJ3D0Lh87Zna/5QekoDwa3SqYT8CWLWfzhYN4yqjvK3HwqUHRcm7Tm1oJYWiUpnbf9/x7mieYAnN/" set security forwarding-options family inet6 mode flow-based set security nat source rule-set V64-src from zone CLIENTS set security nat source rule-set V64-src to zone WAN set security nat source rule-set V64-src rule 01 match source-address 2001:d88::/64 set security nat source rule-set V64-src rule 01 match destination-address 172.16.7.100/32 set security nat source rule-set V64-src rule 01 then source-nat interface set security nat static rule-set V64 from zone CLIENTS set security nat static rule-set V64 rule 01 match destination-address 2001:d88::253/128 set security nat static rule-set V64 rule 01 then static-nat prefix 172.16.7.100/32 set security nat proxy-ndp interface ge-0/0/1.0 address 2001:d88::253/128 set security policies from-zone CLIENTS to-zone WAN policy P64 match source-address any set security policies from-zone CLIENTS to-zone WAN policy P64 match destination-address any set security policies from-zone CLIENTS to-zone WAN policy P64 match application any set security policies from-zone CLIENTS to-zone WAN policy P64 then permit set security zones security-zone WAN interfaces ge-0/0/4.0 host-inbound-traffic system-services ping set security zones security-zone CLIENTS interfaces ge-0/0/1.0 host-inbound-traffic system-services ping set interfaces ge-0/0/1 unit 0 family inet6 address 2001:d88::1/64 set interfaces ge-0/0/4 unit 0 family inet address 172.16.2.2/24 set routing-options static route 0.0.0.0/0 next-hop 172.16.2.1 set routing-options static route 0.0.0.0/0 preference 255
Pisces:
set version 17.3R1-S1.6 set system host-name Pisces set system time-zone Europe/Berlin set system management-instance set system root-authentication encrypted-password "$6$6s/YdPmc$90tCKZVCyj46dNrOPlj1wlQU.ieTTJtuELT2sUNC8dOF8GtyKxmwPwbhG9ZXFiM.KCN.eHkY4hBJpuUdM6BCk/" set interfaces ge-0/0/0 unit 0 family inet address 10.10.0.2/24 set interfaces ge-0/0/2 unit 0 family inet address 192.168.0.133/24 set interfaces ge-0/0/3 unit 0 family inet address 172.16.1.1/24 set interfaces ge-0/0/4 unit 0 family inet address 172.16.2.1/24 set routing-options static route 0.0.0.0/0 next-hop 192.168.0.254 set routing-options static route 0.0.0.0/0 preference 255 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface ge-0/0/3.0 passive set protocols ospf area 0.0.0.0 interface ge-0/0/4.0 passive
Pyxis:
set version 17.3R1-S1.6 set system host-name Pyxis set system root-authentication encrypted-password "$6$v9SuA11k$QrLyhORoCn6JZlQ5zb9SeZ.e30ePX8AumXv2xbQZNs12JOvmoM9dbBa7TJOijtdDz2QiThnTRxETqpaoD.oz//" set interfaces ge-0/0/0 unit 0 family inet address 10.10.0.1/24 set interfaces ge-0/0/2 unit 0 family inet address 192.168.0.143/24 set interfaces ge-0/0/5 unit 0 family inet address 172.16.3.1/24 set interfaces ge-0/0/6 unit 0 family inet address 172.16.4.1/24 set routing-options static route 0.0.0.0/0 next-hop 192.168.0.254 set routing-options static route 0.0.0.0/0 preference 255 set routing-options static route 172.16.7.0/24 next-hop 172.16.3.2 set protocols ospf export OSPF_ext set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface ge-0/0/5.0 passive set protocols ospf area 0.0.0.0 interface ge-0/0/6.0 passive set policy-options policy-statement OSPF_ext from protocol static set policy-options policy-statement OSPF_ext then accept
Virgo:
set version 17.3R1-S1.6 set system host-name Virgo set system root-authentication encrypted-password "$6$JlBYr7De$HiDZ2uPKQrJ3D0Lh87Zna/5QekoDwa3SqYT8CWLWfzhYN4yqjvK3HwqUHRcm7Tm1oJYWiUpnbf9/x7mieYAnN/" set security policies from-zone WAN to-zone DMZ policy P64 match source-address any set security policies from-zone WAN to-zone DMZ policy P64 match destination-address any set security policies from-zone WAN to-zone DMZ policy P64 match application any set security policies from-zone WAN to-zone DMZ policy P64 then permit set security zones security-zone WAN interfaces ge-0/0/5.0 host-inbound-traffic system-services ping set security zones security-zone DMZ interfaces ge-0/0/1.0 host-inbound-traffic system-services ping set interfaces ge-0/0/1 unit 0 family inet address 172.16.7.1/24 set interfaces ge-0/0/5 unit 0 family inet address 172.16.3.2/24 set routing-options static route 0.0.0.0/0 next-hop 172.16.3.1 set routing-options static route 0.0.0.0/0 preference 255