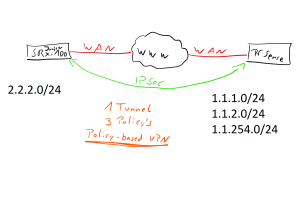
Today (with the help of my friend and skillful netadmin Malte) we finally figured out how to bring up an IPsec Site-to-Site Policy-based VPN with multiple phase2-entries behind the PfSense and a single subnet behind the SRX100.
For this to work with a Policy-Based VPN (since PfSense can’t do route-based VPN) you need to create a policy for each combination of the subnets so that juniper can generate the correct proxy-id’s. If you miss one, you end up with an error like:
Last Tunnel Down Reason: More than two SA pairs
Here’s the config from the J-Point of view:
set security ike proposal ike-proposal-colocation authentication-method pre-shared-keys set security ike proposal ike-proposal-colocation dh-group group2 set security ike proposal ike-proposal-colocation authentication-algorithm sha-256 set security ike proposal ike-proposal-colocation encryption-algorithm aes-256-cbc set security ike proposal ike-proposal-colocation lifetime-seconds 28800 set security ike policy ike-policy-colocation mode aggressive set security ike policy ike-policy-colocation proposals ike-proposal-colocation set security ike policy ike-policy-colocation pre-shared-key ascii-text <SECRET> set security ike gateway ike-gate-colocation ike-policy ike-policy-colocation set security ike gateway ike-gate-colocation dynamic hostname <HOSTNAME colocation> set security ike gateway ike-gate-colocation local-identity hostname <LOCAL HOSTNAME> set security ike gateway ike-gate-colocation external-interface fe-0/0/0 set security ipsec proposal ipsec-proposal-colocation protocol esp set security ipsec proposal ipsec-proposal-colocation authentication-algorithm hmac-sha-256-128 set security ipsec proposal ipsec-proposal-colocation encryption-algorithm 3des-cbc set security ipsec proposal ipsec-proposal-colocation lifetime-seconds 3600 set security ipsec policy ipsec-policy-colocation proposals ipsec-proposal-colocation set security ipsec vpn ipsec-vpn-colocation ike gateway ike-gate-colocation set security ipsec vpn ipsec-vpn-colocation ike ipsec-policy ipsec-policy-colocation set security ipsec vpn ipsec-vpn-colocation establish-tunnels immediately set security address-book global address NW_loc2_1-1-1 1.1.1.0/24 set security address-book global address NW_loc2_1-1-2 1.1.2.0/24 set security address-book global address NW_loc2_1-1-254 1.1.254.0/24 set security address-book global address NW_Local_LAN 2.2.2.0/24 set security policies from-zone external to-zone junos-host policy allow-icmp-any match source-address any set security policies from-zone external to-zone junos-host policy allow-icmp-any match destination-address SRX-WAN set security policies from-zone external to-zone junos-host policy allow-icmp-any match application junos-ping set security policies from-zone external to-zone junos-host policy allow-icmp-any match application junos-ike set security policies from-zone external to-zone junos-host policy allow-icmp-any match application custom-ipsec set security policies from-zone external to-zone junos-host policy allow-icmp-any then permit set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-1 match source-address NW_loc2_1-1-1 set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-1 match destination-address NW_Local_LAN set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-1 match application any set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-1 then permit tunnel ipsec-vpn ipsec-vpn-colocation set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-1 then permit tunnel pair-policy vpnpolicy-internal-colocation-1 set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-2 match source-address NW_loc2_1-1-2 set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-2 match destination-address NW_Local_LAN set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-2 match application any set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-2 then permit tunnel ipsec-vpn ipsec-vpn-colocation set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-2 then permit tunnel pair-policy vpnpolicy-internal-colocation-2 set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-3 match source-address NW_loc2_1-1-254 set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-3 match destination-address NW_Local_LAN set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-3 match application any set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-3 then permit tunnel ipsec-vpn ipsec-vpn-colocation set security policies from-zone external to-zone internal policy vpnpolicy-colocation-internal-3 then permit tunnel pair-policy vpnpolicy-internal-colocation-3 set security nat source rule-set internal-to-external from zone internal set security nat source rule-set internal-to-external to zone external set security nat source rule-set internal-to-external rule no-nat-internal match source-address 2.2.2.0/24 set security nat source rule-set internal-to-external rule no-nat-internal match destination-address 1.1.1.0/24 set security nat source rule-set internal-to-external rule no-nat-internal match destination-address 2.2.21.0/24 set security nat source rule-set internal-to-external rule no-nat-internal then source-nat off set security nat source rule-set internal-to-external rule nat-internal match source-address 2.2.2.0/24 set security nat source rule-set internal-to-external rule nat-internal match destination-address 0.0.0.0/0 set security nat source rule-set internal-to-external rule nat-internal then source-nat interface set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-1 match source-address NW_Local_LAN set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-1 match destination-address NW_loc2_1-1-1 set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-1 match application any set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-1 then permit tunnel ipsec-vpn ipsec-vpn-colocation set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-1 then permit tunnel pair-policy vpnpolicy-colocation-internal-1 set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-2 match source-address NW_Local_LAN set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-2 match destination-address NW_loc2_1-1-2 set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-2 match application any set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-2 then permit tunnel ipsec-vpn ipsec-vpn-colocation set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-2 then permit tunnel pair-policy vpnpolicy-colocation-internal-2 set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-3 match source-address NW_Local_LAN set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-3 match destination-address NW_loc2_1-1-254 set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-3 match application any set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-3 then permit tunnel ipsec-vpn ipsec-vpn-colocation set security policies from-zone internal to-zone external policy vpnpolicy-internal-colocation-3 then permit tunnel pair-policy vpnpolicy-colocation-internal-3 set applications application custom-ipsec protocol udp set applications application custom-ipsec destination-port 4500 set security zones security-zone external host-inbound-traffic system-services ike
Took us some time to figure out why we still had some problems but in the end we found the culprit:
security ipsec policy ipsec-policy-colocation perfect-forward-secrecy keys group5
Seems to me, that PfSense and Juniper don’t play very nice when PFS is enabled.
After deleting the PFS-Group all 3 subnets went up and traffic was able to flow.
Hopefully this short article can save you some pain in the ass 😉
Christian, do you happen to have the PFSense config still (I see the post is old so no worries if not)?
Hi Gary,
I might indeed be able to fetch it from my Archives – I will see what I can find
But remember: this is still an old Version of PFSense and an SRX100 that we are talking about.
Nowadays, there are many secure ways to connect PFSense and the SRX300, for example.
–Christian
Hello,
Are there any ideas how to do some workaround to enable access to srx mgmt interface via Policy-based VPN tunnel? or it seems the routle policy based is the only option here?
I tried route leaking but still it didn’t help to enable access to SRX MGMT interface (FXP0) via Policy-Base vpn tunnel.
I think since Policy-Based vpn required external interface and related static route to be in the main routing table as FXP0 so the traffic targeted to FXP0 will always prefer the Local interface (FXP0) rather than sending it to another instance then sending it to FXP0 via some mgmt switch.
I personally don’t think you should try to manipulate the fxp that way – better use the “inband” method and allow the necessary services.
— Christian