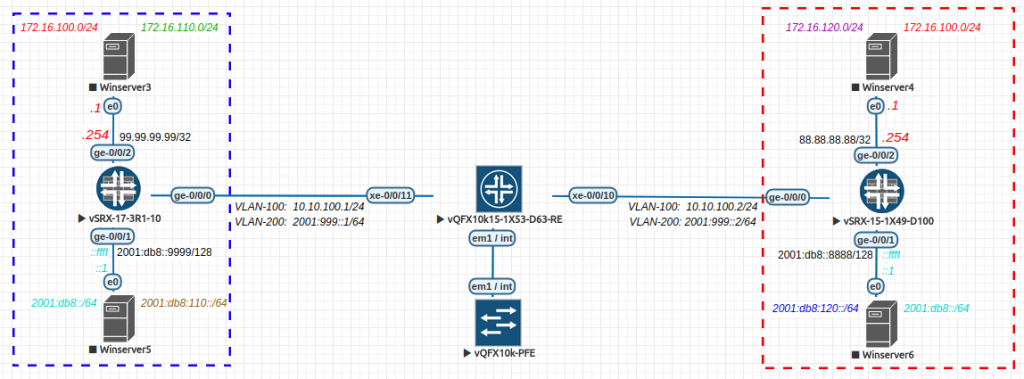
On my way to JNCIE, NAT64 is also a Topic – below you will find a working example of how I achieved this – comments are welcomed 🙂
Site 1 (running 15.1 code)
root@vSRX-15.1X49-D100> show configuration | display set | no-more set version 15.1X49-D100.6 set system host-name vSRX-15.1X49-D100 set system root-authentication encrypted-password "$5$oAlcMo29$MTj5S03CKi45fpyJ9qtT26dCwD48K9l1Cc3muAOzF11" set system services ssh set system services web-management http interface fxp0.0 set system syslog user * any emergency set system syslog file messages any any set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security log mode stream set security log report set security nat source pool src-pool-120 address 172.16.120.0/24 set security nat source pool src-pool-120v6 address 2001:db8:120::/64 set security nat source rule-set rs-v4-out from zone DMZv4 set security nat source rule-set rs-v4-out to zone trust set security nat source rule-set rs-v4-out rule r1 match source-address 172.16.100.0/24 set security nat source rule-set rs-v4-out rule r1 match destination-address 172.16.110.0/24 set security nat source rule-set rs-v4-out rule r1 then source-nat pool src-pool-120 set security nat source rule-set rs-v6-out from zone DMZv6 set security nat source rule-set rs-v6-out to zone trust set security nat source rule-set rs-v6-out rule r1v6 match source-address 2001:db8::/64 set security nat source rule-set rs-v6-out rule r1v6 match destination-address 2001:db8:110::/64 set security nat source rule-set rs-v6-out rule r1v6 then source-nat pool src-pool-120v6 set security nat source rule-set V64-src from zone DMZv6 set security nat source rule-set V64-src to zone DMZv4 set security nat source rule-set V64-src rule 1 match source-address 2001:db8::/64 set security nat source rule-set V64-src rule 1 match destination-address 172.16.100.1/32 set security nat source rule-set V64-src rule 1 then source-nat interface set security nat destination pool dst-v4-pool address 172.16.100.1/32 set security nat destination pool dst-v6-pool address 2001:db8::1/128 set security nat destination rule-set dst-v4-in from zone trust set security nat destination rule-set dst-v4-in rule r1 match destination-address 172.16.120.1/32 set security nat destination rule-set dst-v4-in rule r1 then destination-nat pool dst-v4-pool set security nat destination rule-set dst-v4-in rule r1v6 match destination-address 2001:db8:120::1/128 set security nat destination rule-set dst-v4-in rule r1v6 then destination-nat pool dst-v6-pool set security nat static rule-set V64 from zone DMZv6 set security nat static rule-set V64 rule 1 match destination-address 2001:db8::8888/128 set security nat static rule-set V64 rule 1 then static-nat prefix 172.16.100.1/32 set security nat static rule-set v46 from zone DMZv4 set security nat static rule-set v46 rule 2 match source-address 172.16.100.1/32 set security nat static rule-set v46 rule 2 match destination-address 88.88.88.88/32 set security nat static rule-set v46 rule 2 then static-nat prefix 2001:db8::1/128 set security nat proxy-arp interface ge-0/0/0.100 address 172.16.120.1/32 set security nat proxy-arp interface ge-0/0/2.0 address 88.88.88.88/32 set security nat proxy-ndp interface ge-0/0/0.200 address 2001:db8:120::1/128 set security nat proxy-ndp interface ge-0/0/1.0 address 2001:db8::8888/128 set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone DMZv4 policy Policy01 match source-address any set security policies from-zone trust to-zone DMZv4 policy Policy01 match destination-address any set security policies from-zone trust to-zone DMZv4 policy Policy01 match application any set security policies from-zone trust to-zone DMZv4 policy Policy01 then permit set security policies from-zone DMZv4 to-zone trust policy Policy01 match source-address any set security policies from-zone DMZv4 to-zone trust policy Policy01 match destination-address any set security policies from-zone DMZv4 to-zone trust policy Policy01 match application any set security policies from-zone DMZv4 to-zone trust policy Policy01 then permit set security policies from-zone trust to-zone DMZv6 policy Policy01 match source-address any set security policies from-zone trust to-zone DMZv6 policy Policy01 match destination-address any set security policies from-zone trust to-zone DMZv6 policy Policy01 match application any set security policies from-zone trust to-zone DMZv6 policy Policy01 then permit set security policies from-zone DMZv6 to-zone trust policy Policy01 match source-address any set security policies from-zone DMZv6 to-zone trust policy Policy01 match destination-address any set security policies from-zone DMZv6 to-zone trust policy Policy01 match application any set security policies from-zone DMZv6 to-zone trust policy Policy01 then permit set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 match source-address any set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 match destination-address any set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 match application any set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 then permit set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 match source-address any set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 match destination-address any set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 match application any set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 then permit set security zones security-zone trust tcp-rst set security zones security-zone trust interfaces ge-0/0/0.100 host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/0.100 host-inbound-traffic system-services ssh set security zones security-zone trust interfaces ge-0/0/0.200 host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/0.200 host-inbound-traffic system-services ssh set security zones security-zone DMZv4 interfaces ge-0/0/2.0 host-inbound-traffic system-services ping set security zones security-zone DMZv6 interfaces ge-0/0/1.0 host-inbound-traffic system-services ping set interfaces ge-0/0/0 vlan-tagging set interfaces ge-0/0/0 unit 100 vlan-id 100 set interfaces ge-0/0/0 unit 100 family inet address 10.10.100.2/24 set interfaces ge-0/0/0 unit 200 vlan-id 200 set interfaces ge-0/0/0 unit 200 family inet6 address 2001:999::2/64 set interfaces ge-0/0/1 unit 0 family inet6 address 2001:db8::ffff/64 set interfaces ge-0/0/2 unit 0 family inet address 172.16.100.254/24 set interfaces fxp0 unit 0 set routing-options rib inet6.0 static route 2001:db8:110::/64 next-hop 2001:999::1 set routing-options static route 172.16.110.0/24 next-hop 10.10.100.1
Site 2 (running 17.3 code)
root@vSRX-17.3R1> show configuration | display set | no-more set version 17.3R1.10 set system host-name vSRX-17.3R1 set system root-authentication encrypted-password "$6$6FZUak4n$6INXuka82AT9lXhhvNmBPd8KQa0gokqcOwV1.MFqsrwqNY0DInH2EggK8vQUDXJHJpX.CDZ466cGLP.NB/Bf81" set system services ssh set system services web-management http interface fxp0.0 set system syslog user * any emergency set system syslog file messages any any set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set security nat source pool src-pool-110 address 172.16.110.0/24 set security nat source pool src-pool-110v6 address 2001:db8:110::/64 set security nat source rule-set rs-v4-out from zone DMZv4 set security nat source rule-set rs-v4-out to zone trust set security nat source rule-set rs-v4-out rule r1 match source-address 172.16.100.0/24 set security nat source rule-set rs-v4-out rule r1 match destination-address 172.16.120.0/24 set security nat source rule-set rs-v4-out rule r1 then source-nat pool src-pool-110 set security nat source rule-set rs-v6-out from zone DMZv6 set security nat source rule-set rs-v6-out to zone trust set security nat source rule-set rs-v6-out rule r1v6 match source-address 2001:db8::/64 set security nat source rule-set rs-v6-out rule r1v6 match destination-address 2001:db8:120::/64 set security nat source rule-set rs-v6-out rule r1v6 then source-nat pool src-pool-110v6 set security nat source rule-set V64-src from zone DMZv6 set security nat source rule-set V64-src to zone DMZv4 set security nat source rule-set V64-src rule 1 match source-address 2001:db8::/64 set security nat source rule-set V64-src rule 1 match destination-address 172.16.100.1/32 set security nat source rule-set V64-src rule 1 then source-nat interface set security nat destination pool dst-v4-pool address 172.16.100.1/32 set security nat destination pool dst-v6-pool address 2001:db8::1/128 set security nat destination rule-set dst-v4-in from zone trust set security nat destination rule-set dst-v4-in rule r1 match destination-address 172.16.110.1/32 set security nat destination rule-set dst-v4-in rule r1 then destination-nat pool dst-v4-pool set security nat destination rule-set dst-v4-in rule r1v6 match destination-address 2001:db8:110::1/128 set security nat destination rule-set dst-v4-in rule r1v6 then destination-nat pool dst-v6-pool set security nat static rule-set V64 from zone DMZv6 set security nat static rule-set V64 rule 1 match destination-address 2001:db8::9999/128 set security nat static rule-set V64 rule 1 then static-nat prefix 172.16.100.1/32 set security nat static rule-set v46 from zone DMZv4 set security nat static rule-set v46 rule 2 match source-address 172.16.100.1/32 set security nat static rule-set v46 rule 2 match destination-address 99.99.99.99/32 set security nat static rule-set v46 rule 2 then static-nat prefix 2001:db8::1/128 set security nat proxy-arp interface ge-0/0/0.100 address 172.16.110.1/32 set security nat proxy-arp interface ge-0/0/2.0 address 99.99.99.99/32 set security nat proxy-ndp interface ge-0/0/0.200 address 2001:db8:110::1/128 set security nat proxy-ndp interface ge-0/0/1.0 address 2001:db8::9999/128 set security policies from-zone trust to-zone trust policy default-permit match source-address any set security policies from-zone trust to-zone trust policy default-permit match destination-address any set security policies from-zone trust to-zone trust policy default-permit match application any set security policies from-zone trust to-zone trust policy default-permit then permit set security policies from-zone trust to-zone DMZv4 policy Policy01 match source-address any set security policies from-zone trust to-zone DMZv4 policy Policy01 match destination-address any set security policies from-zone trust to-zone DMZv4 policy Policy01 match application any set security policies from-zone trust to-zone DMZv4 policy Policy01 then permit set security policies from-zone DMZv4 to-zone trust policy Policy01 match source-address any set security policies from-zone DMZv4 to-zone trust policy Policy01 match destination-address any set security policies from-zone DMZv4 to-zone trust policy Policy01 match application any set security policies from-zone DMZv4 to-zone trust policy Policy01 then permit set security policies from-zone trust to-zone DMZv6 policy Policy01 match source-address any set security policies from-zone trust to-zone DMZv6 policy Policy01 match destination-address any set security policies from-zone trust to-zone DMZv6 policy Policy01 match application any set security policies from-zone trust to-zone DMZv6 policy Policy01 then permit set security policies from-zone DMZv6 to-zone trust policy Policy01 match source-address any set security policies from-zone DMZv6 to-zone trust policy Policy01 match destination-address any set security policies from-zone DMZv6 to-zone trust policy Policy01 match application any set security policies from-zone DMZv6 to-zone trust policy Policy01 then permit set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 match source-address any set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 match destination-address any set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 match application any set security policies from-zone DMZv4 to-zone DMZv6 policy Policy01 then permit set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 match source-address any set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 match destination-address any set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 match application any set security policies from-zone DMZv6 to-zone DMZv4 policy Policy01 then permit set security zones security-zone trust tcp-rst set security zones security-zone trust interfaces ge-0/0/0.100 host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/0.100 host-inbound-traffic system-services ssh set security zones security-zone trust interfaces ge-0/0/0.200 host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/0.200 host-inbound-traffic system-services ssh set security zones security-zone DMZv4 interfaces ge-0/0/2.0 host-inbound-traffic system-services ping set security zones security-zone DMZv6 interfaces ge-0/0/1.0 host-inbound-traffic system-services ping set interfaces ge-0/0/0 vlan-tagging set interfaces ge-0/0/0 unit 100 vlan-id 100 set interfaces ge-0/0/0 unit 100 family inet address 10.10.100.1/24 set interfaces ge-0/0/0 unit 200 vlan-id 200 set interfaces ge-0/0/0 unit 200 family inet6 address 2001:999::1/64 set interfaces ge-0/0/1 unit 0 family inet6 address 2001:db8::ffff/64 set interfaces ge-0/0/2 unit 0 family inet address 172.16.100.254/24 set interfaces fxp0 unit 0 set routing-options rib inet6.0 static route 2001:db8:120::/64 next-hop 2001:999::2 set routing-options static route 172.16.120.0/24 next-hop 10.10.100.2
Hope this helps you all