As part of my JNCIE-ENT study, GRE-Tunnels are also a topic.
Turns out, that GRE-Tunnels are quite simple to set up and give you a lot of Flexibility.
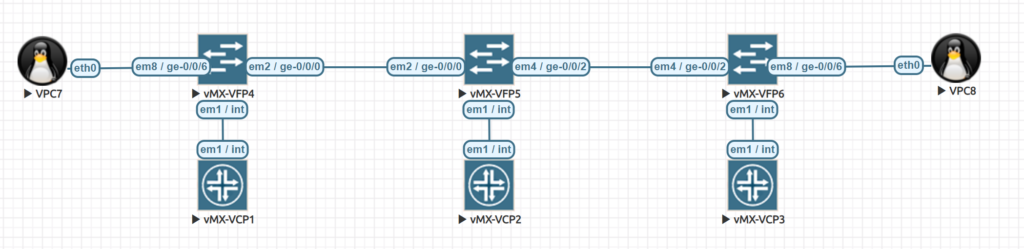
In this Topology, the network 172.16.1.x/24 is behind vMX-VFP6 (VPC8) and the network 172.16.2.x/24 is behind vMX-VFP4 (VPC7). Our middle Router, vMX-VFP5/ vMX-VCP2 is not aware of the 172 networks and has no route at all towards the networks. VCP1 and VCP3 are out Tunnel-Endpoints and are configured like this:
VCP-1:
set system root-authentication encrypted-password "$6$PyP6cuVZ$HY8kv92ln9xXdkJEIp0EyI1PBie4/oH//pxBi9gau2.scpFFuAcu8620bpLk3TuhABQGuVDQ5Dgx7.b64GKDT1"
set chassis fpc 0 pic 0 tunnel-services bandwidth 10g
set interfaces ge-0/0/0 unit 0 family inet address 192.168.0.5/30
set interfaces gr-0/0/0 unit 0 tunnel source 10.10.10.1
set interfaces gr-0/0/0 unit 0 tunnel destination 10.10.10.2
set interfaces gr-0/0/0 unit 0 tunnel allow-fragmentation
set interfaces gr-0/0/0 unit 0 tunnel path-mtu-discovery
set interfaces gr-0/0/0 unit 0 family inet address 172.16.0.1/30
set interfaces ge-0/0/6 unit 0 family inet address 172.16.2.1/24
set interfaces lo0 unit 0 family inet address 10.10.10.1/32
set routing-options static route 0.0.0.0/0 next-hop 192.168.0.6
set routing-options static route 172.16.1.0/24 next-hop gr-0/0/0.0
root> show route
inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:17:48
> to 192.168.0.6 via ge-0/0/0.0
10.10.10.1/32 *[Direct/0] 00:22:52
> via lo0.0
172.16.0.0/30 *[Direct/0] 00:06:16
> via gr-0/0/0.0
172.16.0.1/32 *[Local/0] 00:06:16
Local via gr-0/0/0.0
172.16.1.0/24 *[Static/5] 00:06:16
> via gr-0/0/0.0
172.16.2.0/24 *[Direct/0] 00:11:25
> via ge-0/0/6.0
172.16.2.1/32 *[Local/0] 00:11:25
Local via ge-0/0/6.0
192.168.0.4/30 *[Direct/0] 00:18:16
> via ge-0/0/0.0
192.168.0.5/32 *[Local/0] 00:18:16
Local via ge-0/0/0.0
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
ff02::2/128 *[INET6/0] 00:26:42
MultiRecvVCP-2:
set system root-authentication encrypted-password "$6$Tc7j6QVB$UQ4WzeKUlcwMyIzJRo4WtRW4/WMAhWlWC/6Pd6RwYatXqEKf40vJxAq28TAnRAsuS8BQugOtyopVSs7nUARbY0"
set interfaces ge-0/0/0 unit 0 family inet address 192.168.0.6/30
set interfaces ge-0/0/2 unit 0 family inet address 192.168.0.2/30
set routing-options static route 10.10.10.1/32 next-hop 192.168.0.5
set routing-options static route 10.10.10.2/32 next-hop 192.168.0.1
root> show route
inet.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
10.10.10.1/32 *[Static/5] 00:14:33
> to 192.168.0.5 via ge-0/0/0.0
10.10.10.2/32 *[Static/5] 00:14:33
> to 192.168.0.1 via ge-0/0/2.0
192.168.0.0/30 *[Direct/0] 00:20:37
> via ge-0/0/2.0
192.168.0.2/32 *[Local/0] 00:20:37
Local via ge-0/0/2.0
192.168.0.4/30 *[Direct/0] 00:19:36
> via ge-0/0/0.0
192.168.0.6/32 *[Local/0] 00:19:36
Local via ge-0/0/0.0
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
ff02::2/128 *[INET6/0] 00:26:51
MultiRecvVCP-3:
set system root-authentication encrypted-password "$6$qe4r6bQM$d/hjo5m/HEiAu4NT47CKzu7S2sxDNczJCfJ0SRQN7/SEnVEoLNekLkhJPZ20aR7K4x0MmIY.mpvPhphvGrPNo."
set chassis fpc 0 pic 0 tunnel-services bandwidth 10g
set interfaces gr-0/0/0 unit 0 tunnel source 10.10.10.2
set interfaces gr-0/0/0 unit 0 tunnel destination 10.10.10.1
set interfaces gr-0/0/0 unit 0 tunnel allow-fragmentation
set interfaces gr-0/0/0 unit 0 tunnel path-mtu-discovery
set interfaces gr-0/0/0 unit 0 family inet address 172.16.0.2/30
set interfaces ge-0/0/2 unit 0 family inet address 192.168.0.1/30
set interfaces ge-0/0/6 unit 0 family inet address 172.16.1.1/24
set interfaces lo0 unit 0 family inet address 10.10.10.2/32
set routing-options static route 0.0.0.0/0 next-hop 192.168.0.2
set routing-options static route 172.16.2.0/24 next-hop gr-0/0/0.0
root> show route
inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:17:46
> to 192.168.0.2 via ge-0/0/2.0
10.10.10.2/32 *[Direct/0] 00:21:50
> via lo0.0
172.16.0.0/30 *[Direct/0] 00:06:31
> via gr-0/0/0.0
172.16.0.2/32 *[Local/0] 00:06:31
Local via gr-0/0/0.0
172.16.1.0/24 *[Direct/0] 00:12:04
> via ge-0/0/6.0
172.16.1.1/32 *[Local/0] 00:12:04
Local via ge-0/0/6.0
172.16.2.0/24 *[Static/5] 00:06:31
> via gr-0/0/0.0
192.168.0.0/30 *[Direct/0] 00:21:14
> via ge-0/0/2.0
192.168.0.1/32 *[Local/0] 00:21:14
Local via ge-0/0/2.0
inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
ff02::2/128 *[INET6/0] 00:26:44
MultiRecvFirst you configure a gr-Interface with a tunnel source and destination.
You also should have a static route to reach the other side of your endpoint!
As you can see in the routing table, VCP2 is not aware of the 172 networks and still VPC7 and VPC8 can issue a ping towards each other, with vPC7 having 172.16.2.100/24 and VPC8 having 172.16.1.100/24 as the host addresses.
Setting up GRE-Tunnels is extremely easy. This allows you to tunnel your networks through your Provider network. But be careful – GRE is not IPsec – especially in terms of security.
Although GRE is able to carry other protocols as well as IP packets in an IP network while IPSec is not, IPsec offers more security than GRE because of its authentication feature.
But do you know the best part? This Lab was done in 6 Minutes (5.5 minutes boot time and the rest configuring) with EVE-NG. As you may have heard, I will soon present a short session about how to use EVE for prepping and labbing – if any of you attend the #NXTWORK2019 you need to check out the Ambassadors Masterclass – especially if you currently use ESX for labbing…