
Slides from Session (Open Learning MIST-Edge and EVE-NG)
As promised, here is the SLidedeck from today’s session 🙂What should we present next for the use of EVE-NG and Juniper? Would deploying EVE-NG as a VM (in various flavors)… Read more »

As promised, here is the SLidedeck from today’s session 🙂What should we present next for the use of EVE-NG and Juniper? Would deploying EVE-NG as a VM (in various flavors)… Read more »

Taking Tuesday’s JNCIE-ENT exam was an experience I will never forget. From the moment I entered the virtual testing center (because sadly it’s still 100% remote only), I felt a… Read more »

Just this week between me and my next JNCIE attempt. Wanna know how it feels every time I post “I’m gonna nail it next time”? 😉

As we traverse the expansive landscape of network protocols, one stands out as a cornerstone, like the granddaddy of routing: OSPF, or Open Shortest Path First. Its dynamic nature and… Read more »

Who said that adam was the first being created by god? I found this antique (okay 3D-printed fresh off the printer) model of Marvis – do you believe us MistFits… Read more »

Great News Folks 🙂I’ve joined a very exclusive group of people united under the banner of Juniper Mist (praise Marvis, our robotic overlord, and savior) to show you all how… Read more »

As you might have heard, last week HPE and Juniper told the world, that HPE will be acquiring Juniper. Nothing more, nothing less. And yet, for some folks this was… Read more »
As we approach the end of 2023, it’s the perfect time to reflect on the achievements and milestones that have shaped my professional year. From personal and professional growth to… Read more »
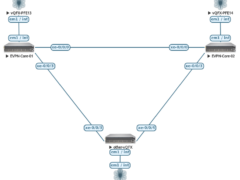
In this example we look at the vQFX “Collapsed-Core” – so a 2-Device EVPN-VXLAN Setup with another vQFX connected to it (called other-vQFX here). Topology: Core-Switch No. 1 – “… Read more »

I’m REALLY REALLY excited to share some news with all of you – those of you who will be in Madrid this July for the TechSummit 2023: Prepare to party… Read more »