
Here is the official “unofficial” Template: vEX-EVEng.zip
Alternative Link: https://jncie.eu/vEX-EVEng.zip
HUGE Shoutouts to everybody who helped to get this up and running during the last few days!
Tippin my Fedora for you 🙂

Here is the official “unofficial” Template: vEX-EVEng.zip
Alternative Link: https://jncie.eu/vEX-EVEng.zip
HUGE Shoutouts to everybody who helped to get this up and running during the last few days!
Tippin my Fedora for you 🙂

As some of you have noticed, we got a little something: https://support.juniper.net/support/downloads/?p=vjunos
That’s right – it’s the new vEX that I already mentioned due to some rumors floating around in my last Webinar is finally out 🙂
It’s available for download now if you have a Juniper Account. Sadly, the image seems to have some issues and unfortunately, no one was reachable yet to discuss these issues from the Juniper side. If you are a Juniper dev for the vEX and like what we do with the EVE-NG Team then please reach out to me directly!
The Version is already fully supported in EVE-NG but there are still a lot of questionmarks left when it comes to the implementation and the configuration.
Hopefully, next time early access is granted to the folks doing extensive testing for virtual solutions (WINK WINK) to be able to solve the first questions BEFORE the image is released – this would have solved some confusion for sure 😉
Anyways – Let’s hope the vEX delivers what was promised (fully integrated into MIST including Campus-Fabric) so that we can finally have a virtual MIST Lab 🙂 I keep you posted once I’ve tested this image extensively myself.
Update 2023-04-25:
Juniper’s vEX (vjunos-switch) dev reached out to me so we can work on the remaining questions 🙂 THANK YOU SO MUCH!
Update 2023-04-26:
Here is the official “unofficial” Template: vEX-EVEng.zip
HUGE Shoutouts to everybody who helped to get this up and running during the last few days!
Tippin my Fedora for you 🙂
Hi all,
as usual, here are the slides from yesterday’s talk 🙂
I do these Webinars regularly – if there’s any specific topic regarding Juniper and EVE-NG reach out to me as I vary the topics from time to time. Ultimately these Webinars are for all of you 🙂
Have you ever encountered this really nasty “bug” where your vQFX will turn into the Linecard (LC) Role? Yeah – welcome to the club!
Thankfully you can avoid this (most of the time if the vQFX shows some mercy) by changing the Serial Number. My guess is, that the vQFX sees the remote PFE with the very same S/N and tries to bind to it – which will fail and therefore put the RE into the LC-state.
First power up your vQFX – you will immediately be presented with the current S/N during the very first messages when the RE boots:
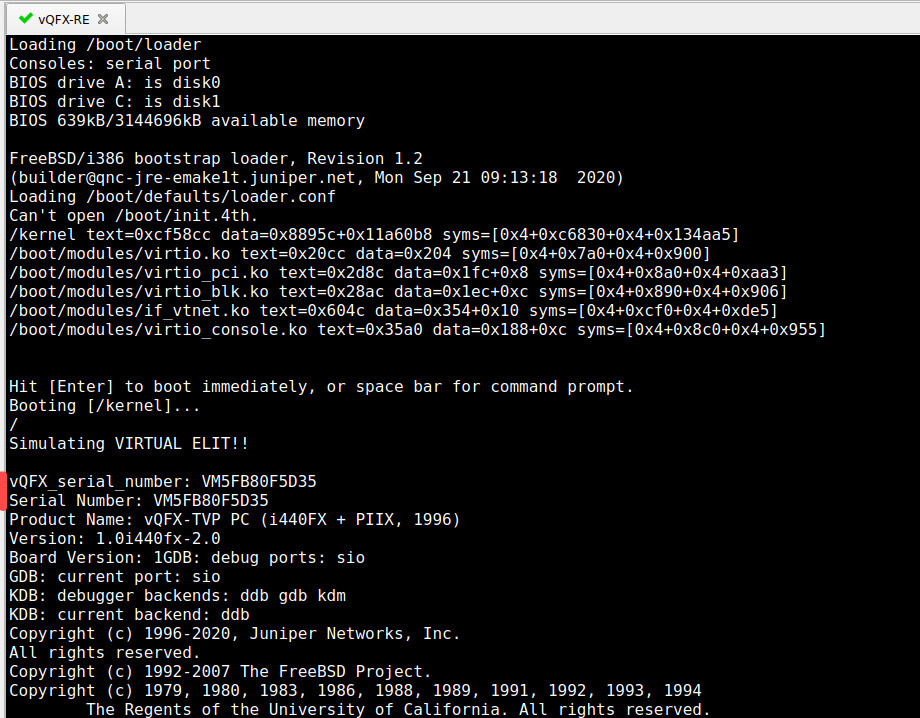
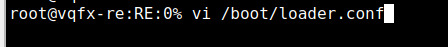
Login as root and edit the file called /boot/loader.conf (trust me, it’s there) 😉
Scroll down to the very bottom and you will see the S/N:
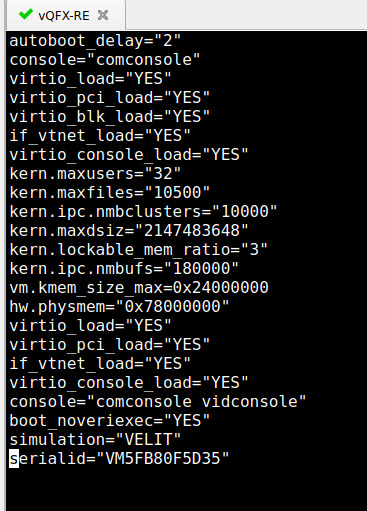
Now you need to know a bit of vi-magic: use the shortcut “dd” to delete the line where your cursor is at (or manually go to the edit mode and delete the last line). Save the file (:wq!) – if you don’t force(!) it, the device will tell you this is a “read-only” permission. After that, reboot the RE.
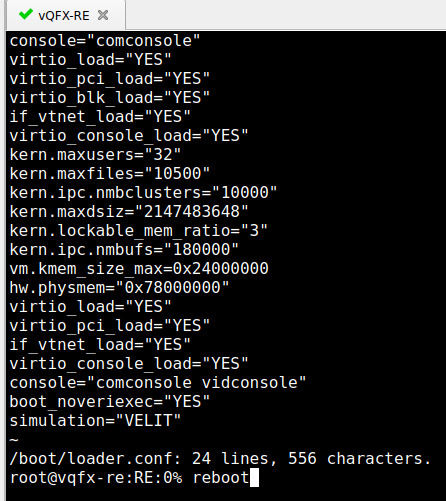
Notice now, that this time during boot, there is no S/N – so the Junos bootup routine will generate a new one for you:
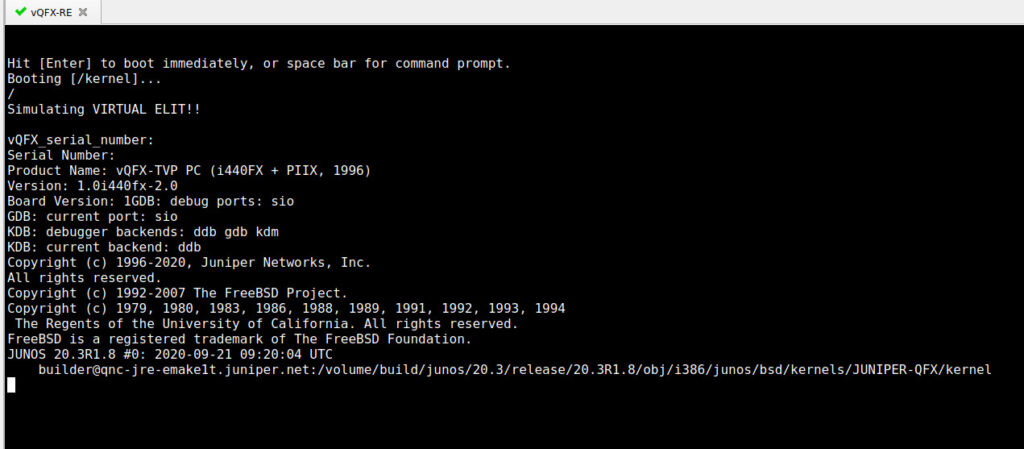
After the device boots, you can either issue “show chassis hardware” or re-enter the same /boot/loader.conf file to see our new and shiny S/N – with this, the vQFX will not try the usual shenanigans again – well, hopefully…
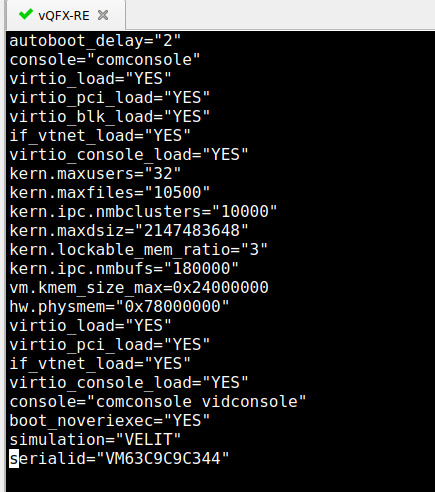
Hope this helps you on your Lab-Quest 🙂
As always – here are the slides from today’s webinar including all the Links needed in order to fetch the vDevices 🙂 If you encounter any problems feel free to reach out to me anytime! Thank you for joining and making these Webinars a success 🙂
If you think Elons Ego couldn’t hit a new low, think again…
Twitter just enforced new Rules:
https://twitter.com/TwitterSupport/status/1604531261791522817
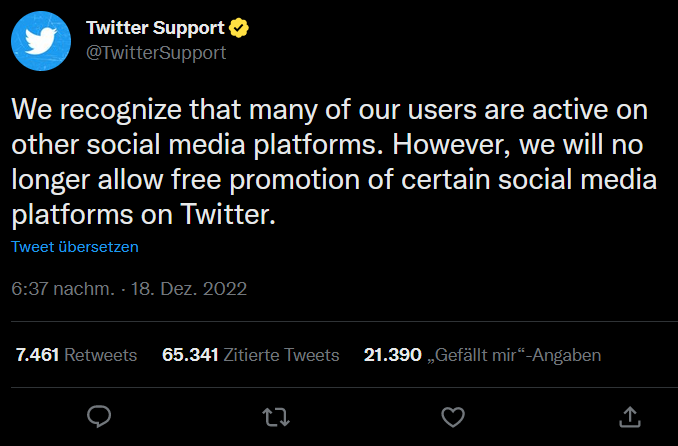
I believe in free speech, a connected and open community, and the right to choose a platform of liking without being “punished” for it. Therefore, I can not and definitely will not accept the new terms of Twitter and will therefore terminate my Account effective immediately! But don’t worry – my main contact point was always here and not on Twitter 😉 You can also:
Follow me on Mastodon: @Juniperchris@mastodon.social | @chsjuniper@mastodon.social
Follow me on LinkedIn: https://www.linkedin.com/in/chsjuniper/
Follow me on YouTube: https://www.youtube.com/netchron/
Follow me in the J-Forum: JChris929 (former CHS-929)
Send me a Mail: chs [at] ip4 {dot} de
What does this mean? Will you delete your profile on twitter?
Not at this time – My Twitter Account will be used as an archive for interested folks but will no longer post any updates or any news.
If you love your garden-power-plant you shouldn’t look at my new DayOneGreen Book 😀
I had some free time and used it to write a teaser for my new book, which will hopefully be published in 2023 🙂
It is extremely important to me to pass on knowledge – that has always been my attitude.
In three examples I will show you how you can save a lot of money by virtualizing your lab environment and at the same time reduce your CO2 footprint – even more with the Juniper vLabs – even in small environments.
Incidentally, at #Axians we are constantly developing new ideas together with #JuniperNetworks to make networks even more efficient and “simpler”. At the end of the day, solutions must also be manageable for small teams – that’s a challenge we accept 😉
Feel free to contact me if you have any questions.
Download the PDF here:
https://www.juniper.net/documentation/en_US/day-one-books/DayOne-Green-vLabs.pdf

Make sure to check out the DayOne Library:
https://www.juniper.net/documentation/jnbooks/us/en/day-one-books
And if you are interested in virtualized Labs here’s the Link to my official OpenLearning Course:
https://learningportal.juniper.net/juniper/user_activity_info.aspx?id=EDU-JUN-WBT-JOL-EVENG
Hi all, here you find (as promised) the slides from my last talk 🙂
If you have any questions or encounter problems feel free to reach out to me 🙂
For a quick “Juniper only” Lab you can also use the vLabs functionality to get started with JunOS and use your EVE-NG Server for your bigger, more customized Labs: https://jlabs.juniper.net/vlabs/
Next week, starting on Oct 17, TechFest2022 is happening 🙂 Unfortunately still virtual – hopefully we will have local TechFests in-person next year. Nevertheless, this TechFest is packed with lots and lots of great Sessions (on-demand sessions). And this one is very special for me because for the very first time I’m not “just” a partner/visitor, but also a speaker – yup – little Christian is finally wearing a bigger pair of pants 😉 Seeing my name next to my idols is somehow terrifying but also exciting at the same time 🙂 I really hope you all enjoy the talk that I had with Ola and the mighty Steve Puluka about automation. Let me know in the comments what sessions you are interested in the most 🙂