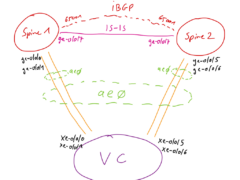
EVPN-VXLAN on the vMX in the Lab
Underlay: IS-IS (to export the lo0 for iBGP)Overlay: iBGP (with evpn signaling enabled)Version: 18.3R3-S4 Spine1: Spine2: VC:

Underlay: IS-IS (to export the lo0 for iBGP)Overlay: iBGP (with evpn signaling enabled)Version: 18.3R3-S4 Spine1: Spine2: VC:

Something good before the weekend starts: Prepare your Labs folks 🙂vEvo is finally here!!!!! Download-Link:https://support.juniper.net/support/downloads/?p=vjunos-evolved Docs: https://www.juniper.net/documentation/us/en/software/vJunosEvolved/vJunosEvolved-kvm-deployment-guide/vJunosEvolved-KVM/topics/vjunosevolved-understand.html More Info soon – happy labbing 🙂 And ICYMI: the new EVE-NG has… Read more »

Here is the official “unofficial” Template: vEX-EVEng.zipAlternative Link: https://jncie.eu/vEX-EVEng.zipHUGE Shoutouts to everybody who helped to get this up and running during the last few days! Tippin my Fedora for you… Read more »
As some of you have noticed, we got a little something: https://support.juniper.net/support/downloads/?p=vjunosThat’s right – it’s the new vEX that I already mentioned due to some rumors floating around in my… Read more »
Hi all, as usual, here are the slides from yesterday’s talk 🙂I do these Webinars regularly – if there’s any specific topic regarding Juniper and EVE-NG reach out to me… Read more »

When Covid really hit everyone I asked my Wife to create this for me 🙂 I designed the Sticker and she filled this with Water (I mean pure concentrated AI… Read more »
Have you ever encountered this really nasty “bug” where your vQFX will turn into the Linecard (LC) Role? Yeah – welcome to the club! Thankfully you can avoid this (most… Read more »
As always – here are the slides from today’s webinar including all the Links needed in order to fetch the vDevices 🙂 If you encounter any problems feel free to… Read more »

If you think Elons Ego couldn’t hit a new low, think again… Twitter just enforced new Rules: https://twitter.com/TwitterSupport/status/1604531261791522817 I believe in free speech, a connected and open community, and the… Read more »

If you love your garden-power-plant you shouldn’t look at my new DayOneGreen Book 😀I had some free time and used it to write a teaser for my new book, which… Read more »